Basics and History of Software Development
Software can be seen as one of the most critical components of a computerized system. Without it, any hardware would be just a useless brick of electronics. Seeing the clear need for a structured approach in developing appropriate software, the discipline of software engineering came up quite early. Different Software Development Lifecycle Models (SDLCs) have emerged over past decades like
- Waterfall
- Iterative and Interactive Development
- Rapid Application Development (RAD)
- Extreme Programming (XP), and more recently
- Agile Methodologies and DevOps
Diagram: Comparison of SDLC Models
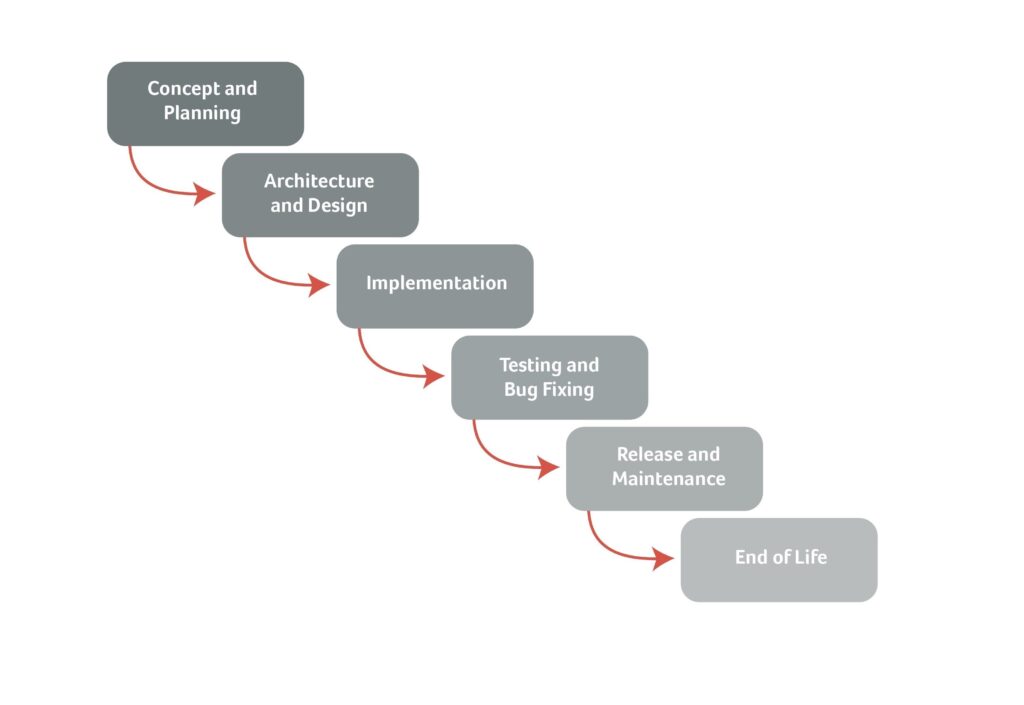
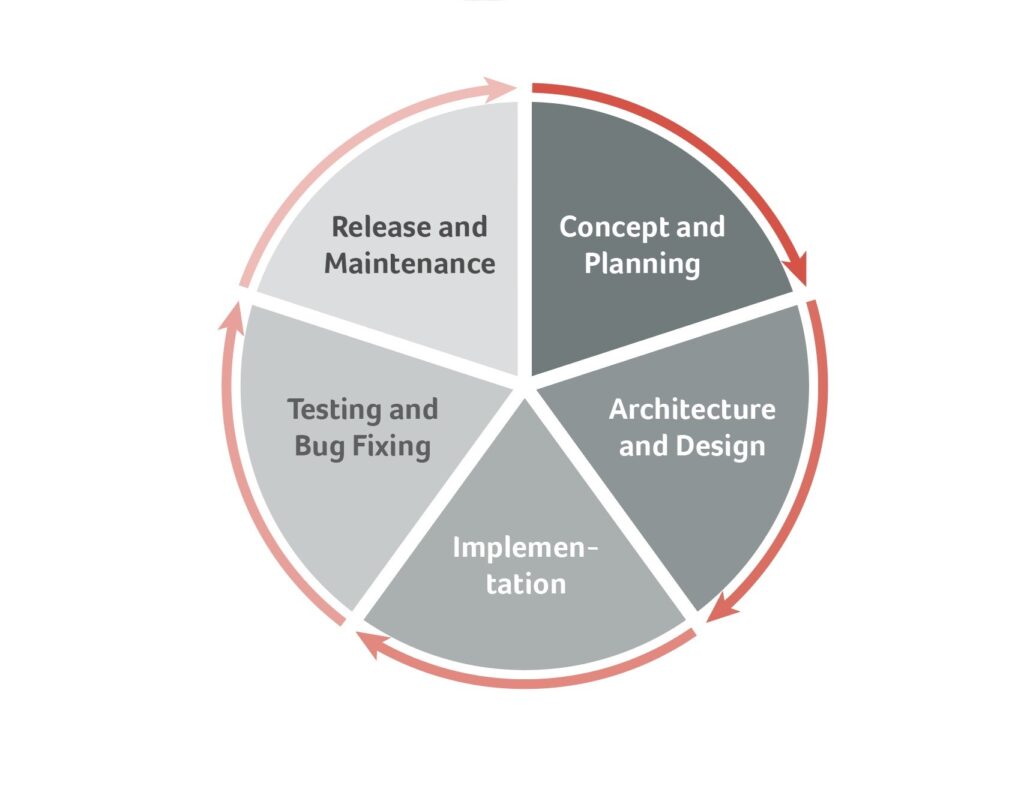
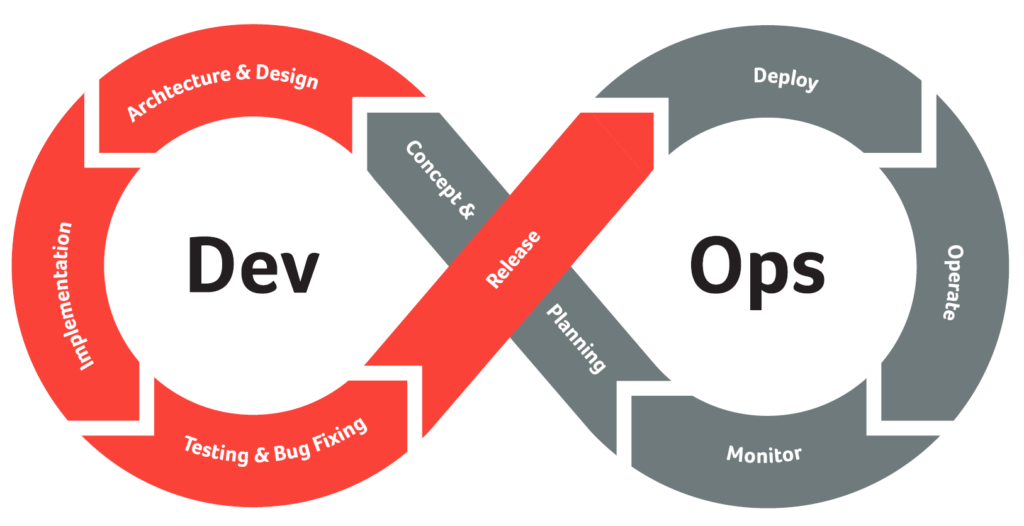
All SDLC models incorporate the idea of a framework for the process of buidling an application from inception to decommission. The objective is to improve quality and to accelerate projects. SDLC models usually include the following basic steps:
- Requirements Gathering and Analysis
- Architecture and Design
- Implementation (Coding)
- Testing and Bug Fixing
- Release (Deployment)
- Maintenance
Functional Testing vs. Security Testing
For a long time, “Testing” in software development was seen as only functional testing. After the coding stage, checks were performed to confirm whether each feature works as per the software requirements and the end users’ expectations.
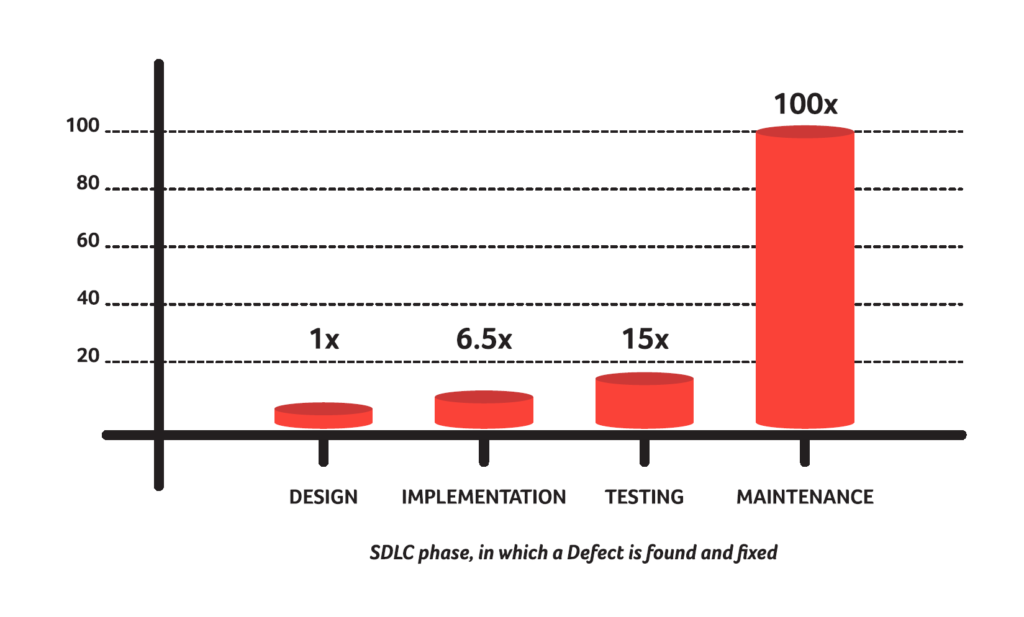
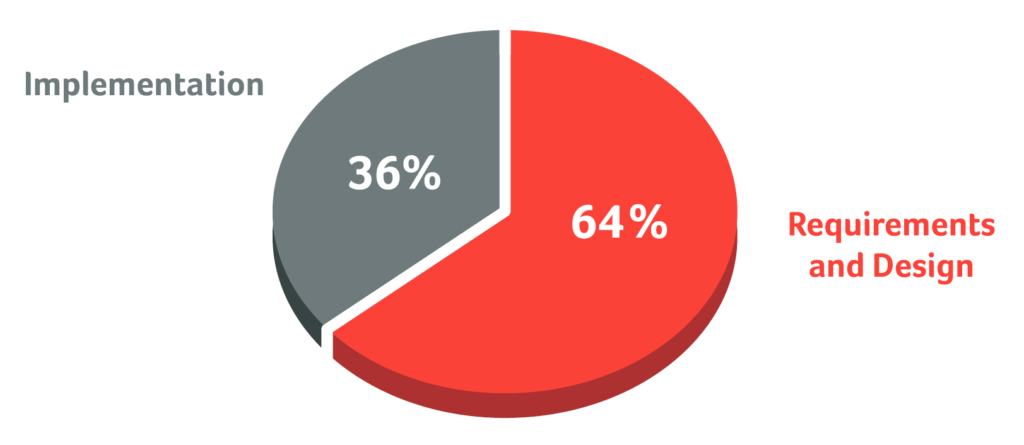
Entering the digital era, it has become an inevitable challenge to focus on security testing as well, in order to identify and prevent defects, vulnerabilities and weaknesses of internet facing applications. To avoid high extra costs of fixing errors and vulnerabilities, their early detection is absolutely necessary (see figure “Relative Costs…”). This approach is called “Shift Left” and is very effective, because the majority of software defects has it’s origin in the early SDLC phases (see figure Origin of…). Moreover it is essential to incorporate security in every phase of the SDLC.
Embedding Security into the SDLC
In recent years, we see cyber criminals becoming more and more professionals. Therefore, the risk of targeted cyber attacks is increasing. These are focusing on dedicated business sectors or even specific companies. For appropriate countermeasures, a structured approach is needed to implement security as an integral building block across the complete SDLC. This adapted lifecycle is called SECURE SDLC or SSDLC with the following advantages:
- More secure software, as security is a continuous concern
- All stakeholders are aware of security considerations (buy-in)
- Early detection of design flaws, before they are coded into existence
- Reduced costs, thanks to early detection and resolution of defects
- Reduced overall intrinsic business risk of an organization
Several SSDLC industry best practice models have been developed and refined over the recent years. They can be divided into two main branches – prescriptive and descriptive models. Figure “Categories of Secure SDLC Models” is showing some examples for each category.
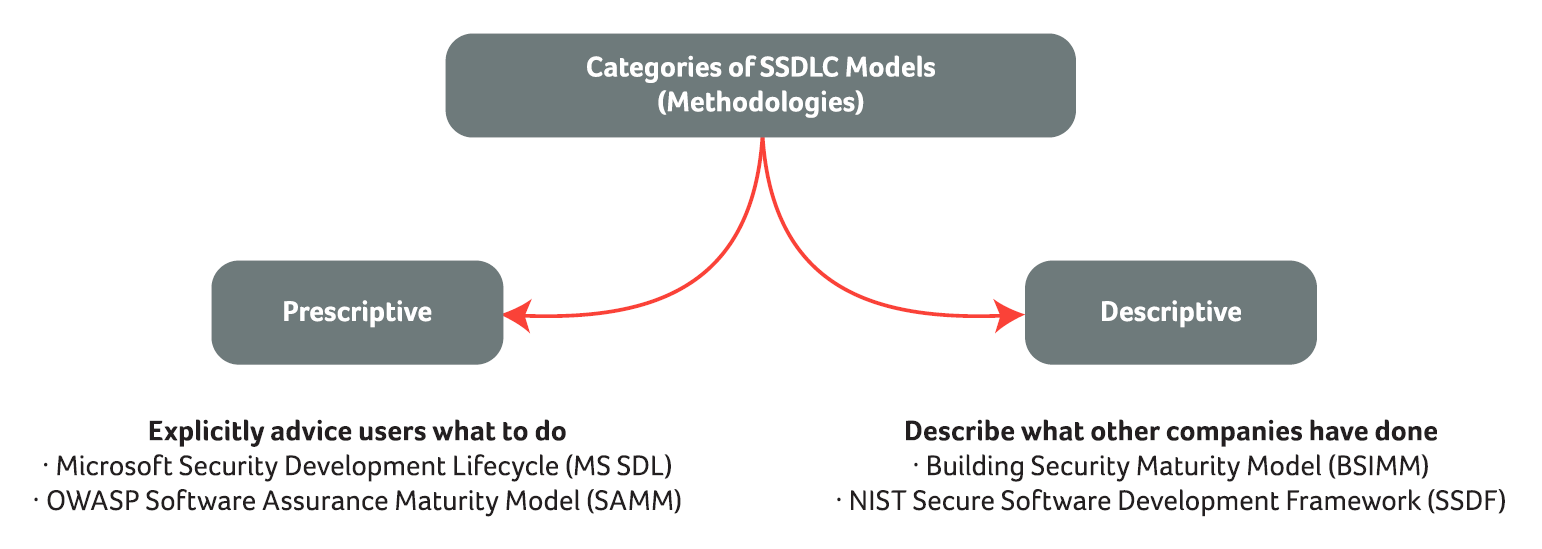
While every model is designed with a certain focus, there is no ‘one size fits all’ solution. But there can be only one advice: take ONE instead of NONE. That means: irrespective of which SSDLC model you prefer to implement for your software development – it is lightyears better than developing “freestyle”.
In the next part, we will deep-dive into more details of different SSDLC models in order to support you find the best fitting model for your organization.