What really takes most of the time of a Software Developer?
Most developers love to focus on programming new features, using sophisticated modern principles and design patterns. When everything works perfectly afterwards and all unit tests pass positively, a sense of success and achievement should await them… in an ideal world…
But the reality is, most of the developers spend around 80% of their time on finding and fixing bugs. This work can be tedious and it is not what developers really enjoy. Especially if this process is really time-consuming.
It is true that the search for errors in code and architecture causes pain and frustration to developers. However, security related bugs or issues cause the most pain to your company. These security issues easily open the door for data breaches and ransomware attacks by those with malicious intent. But they are not easy to identify by modern development environments.
Attackers don’t have a conscience.
- In September 2020, the University Hospital of Düsseldorf was attacked and hackers were able to encrypt 30 servers of the hospital. This resulted in emergency patients not being able to be admitted and cared for. For example, an emergency patient had to be taken to a hospital further away in Wuppertal. It is said that her treatment could only take place after a delay of one hour. Sadly because of this she did not survive. (https://www.nytimes.com/2020/09/18/world/europe/cyber-attack-germany-ransomeware-death.html)
- In April 2023, a cyber-attack on the hospital “Clínic” in Barcelona led to the cancellation of 150 operations and 3000 patient appointments in one day. Even radiation therapy for cancer patients had to be postponed. (https://www.bitdefender.com/blog/hotforsecurity/ransom-house-cybercrime-gang-hits-hospital-clinic-de-barcelona/)

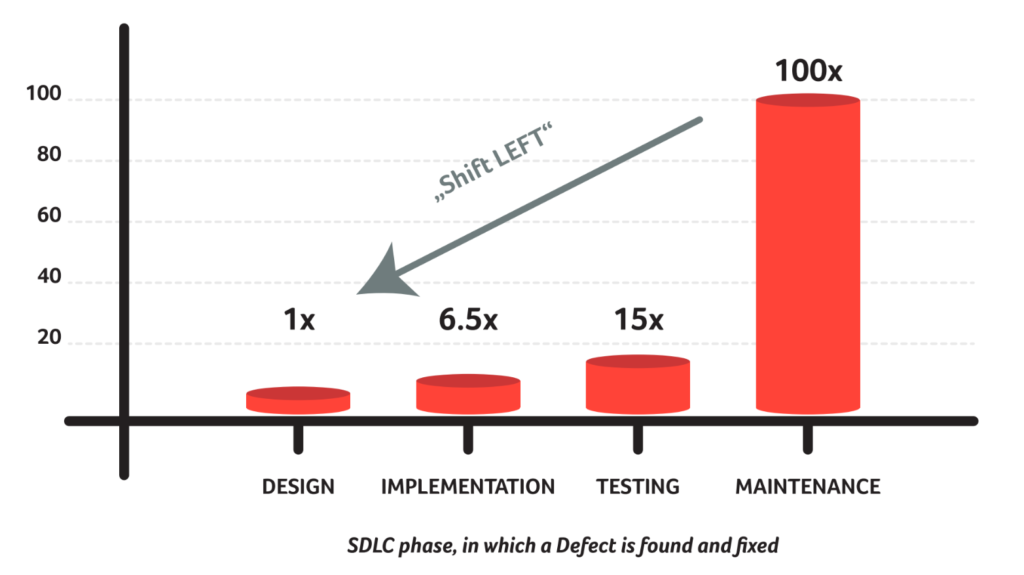
There is also another pain-point for companies regarding software bugs and issues: the cost to fix these issues. The time and the effort to fix issues identified in an already deployed system of a customer, are exponentially much higher than fixing the issues during the design and coding phases of the project.
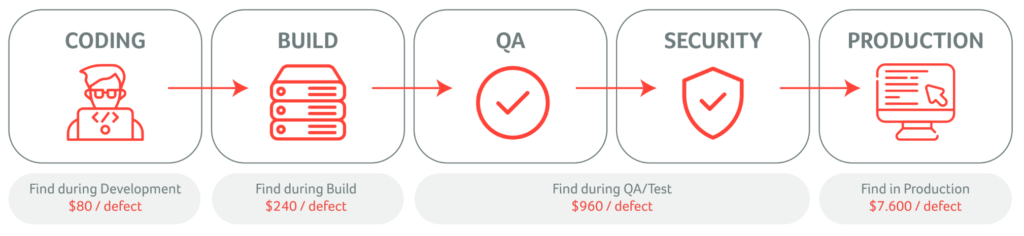
“Shift Left” will reduce costs a hundredfold. This involves finding most of the issues as early as possible or even trying to avoid them during the design phase.
So what does “Shift Left” mean for your company?
Your Developers need:
Training
- Provide Training/Seminars to understand security testing activities for “shifting left” like:
- Static Application Security Testing (SAST)
- Scans only the code of your application and identifies common errors or unsecure parts (white box testing)
- Software Composition Analysis (SCA)
- Focuses on the used libraries and packages to identify known vulnerabilities and even suggests possible upgrade to higher versions to mitigate vulnerabilities
- Dynamic Application Security Testing (DAST)
- DAST testing does not know your code at all (black box testing). Instead, your application will be tested on runtime to identify attack surfaces.
- Static Application Security Testing (SAST)
- Focus on increasing awareness of security issues like the OWASP Top10 vulnerabilities via seminars
- Tip: make use of live Security Training Platforms which include real or simulated Lab environments like https://www.securecodewarrior.com/ or https://portswigger.net/web-security
- Arrange security related monthly talks (Brown Bag Sessions) for the developer community (in person or via video conference)
- The Topics to be discussed in these talks can be proposed and presented by your own developers or you can invite guest speakers to share success stories
- What is a “Brown Bag Session”? A meeting that typically occurs over or during lunch, which uses an informal and often collaborative approach: Attendees are expected to bring their own lunch (hence the name “brown bag”), if they plan to eat during the meetup.
Tools
- IDE (Integrated Development Environment) and extensions like SAST plugins to be able to scan the code before being committed
- DevSecOps: establish a dedicated Engineering Platform with automated CI/CD pipelines scan your code via SAST & DAST and runs containerized apps after being committed to the code repository
- Security Orchestration applications should be in place to follow up with the identified vulnerabilities (best case: transfer of reports integrated in the automated CI pipeline) e.g. OWASP DefectDojo
- Make use of penetration testing toolkits available via Kali Linux (e.g. OWASP ZAP, nmap, Nikto, Burp Suite) to identify attack surfaces.
Experts
- Simulate attacks and identify unknown attack surfaces with the help of Penetration testing teams (internal or external). These Penetration tests need to be mandatory and testing has to be repeated periodically for each major release.
If you would like to know how we can support your company with success-proven processes and initiatives, please contact us at: shift-left-now@anic-gmbh.de